Important note: This article contains information regarding our Dedicated product. If you are looking for documentation regarding the cloud data annotation platform, please visit all other categories in our larger Success Center.
Overview
Before accessing the application, please ensure the following TLS (SSL) certificates are in place. If certificates are not in place, please refer to the “Adding Exceptions” section.
TLS Certificates
Four TLS (SSL) certificates and key pair files are required to be on the control plane before initializing the client. They should all be placed in the /root/tls-certificates/ directory on the control plane VM.
Please note, the file names for a specific domain may vary from the domain prefix, as these file names match the services which use the files, not URL's.
Credentials:
|
Certificate and Key file names |
Valid for Domain |
|
/root/tls-certificates/web.crt /root/tls-certificates/web.key |
*.your.custom.domain.com |
|
/root/tls-certificates/main-nginx.crt /root/tls-certificates/main-nginx.key |
*.your.custom.domain.com |
Applying New TLS (SSL) Certificates to Dedicated
Update all keys and certificates with the appropriate credentials. With the new credentials in place, generate new Cluster “secrets”, apply them to the cluster, and restart all pods that use TLS credentials.
cd ~/ansible-cfsecure
ansible-playbook -i /root/ansible-cfsecure/hosts /root/ansible-cfsecure/play-k8s-kube-configs.yaml --extra-vars='{
"UPDATE_OBJECT":"secret"
}'
for secret in $(ls /root/k8s/secrets/*.yaml); do
kubectl apply -f ${secret};
done
cd /root/k8s/
app="task-force main-nginx requestor-proxy make-web minio worker-ui" ./nuke-and-pave-object.sh
Adding Exceptions
The application URL is accessed over https:// port 443.
| The primary access url for admins and requestors is | app.{{your-custom-domain}}.com/make |
| The primary access url for contributors is | app.{{your-custom-domain}}.com/task-force |
The remaining domains are primarily used by the client code running in the browser to access various APIs, however, they are occasionally used by services within the cluster as well, which is why it is important they resolve both internally and externally.
You may be prompted to allow access due to the insecure connection. Select the “Advanced” setting and set a permanent exception for all ports, when prompted.
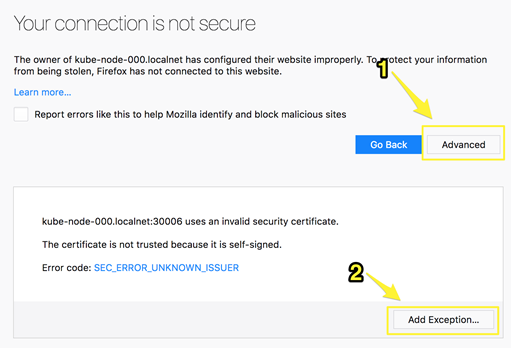
Figure 1: How to add exceptions on Google Chrome
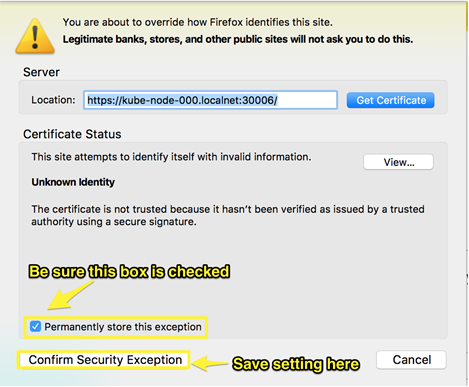
Figure 2: How to add exceptions on Firefox